
Gateway to Digital Economy: How to Remotely Identify and Onboard Customers
(This Part 1 of the series about remote identity verification solutions and how to successfully integrate them into ...
Read more
(This is Part 2 of the series about remote identity verification solutions and how to successfully integrate them into your business. For all parts of the series, click here.)
What you’ll learn in this part:
Before we dive into the specific technologies that make reliable remote identity verification possible, we have to mention just how revolutionary the spread of the smartphone has been for the economy as a whole. Everyone carries it around, it always keeps you connected online, and it contains many elements that make identity verification a breeze.
A typical smartphone has two or more cameras, one of them forward-facing. Its computing power can run neural networks locally and in real time. Furthermore, biometrics – fingerprint and later facial recognition – have become standardized as the technology that unlocks the phone seamlessly.
Building Blocks of Reliable Digital Onboarding
It takes more than just a selfie to ensure that an authorized client is the one using a service. Most technologies work in the background, with the user unaware of what is behind it. All the elements of the digital onboarding process are necessary to make the technology secure and easy to use. The full stack of technologies for ID verification includes:
By using our own top-performing algorithms that are benchmarked by NIST, we are able to instantly verify whether a person is the same as the one we have enrolled previously. The operator gets a numerical value that represents the confidence of the algorithm in the verification process. It doesn’t matter whether the person has a growing stubble or a new haircut, our biometrics can immediately tell whether the person matches the correct user.
Since facial recognition surpassed the human ability to verify the identity of a person over ten years ago, the accuracy of the algorithms has taken huge strides. This is why it is important to make sure that the algorithms you integrate into your solutions are constantly updated. AI-based, machine learning-powered neural networks have increased their accuracy 30-fold in just five years according to NIST.
Facial matching is the most prominent although it has its drawbacks. Most notably, it compares two images and decides how similar the faces are. To avoid being fooled by a photo or a video of an ID fraud victim, you need to perform more checks on your side.

You need to make sure that a person is not using a photo or a mask to impersonate someone else – that’s where liveness detection kicks in. This area is both relatively new and also booming with ideas. The very first solutions have relied on manpower via video calls with call centers, but these have several major drawbacks.
First, they are difficult to scale fast. Second, the human observer is not as accurate as the technology. Lastly, the necessity to call a live person meant that many potential clients – surveys mention 66 to 90 percent – have never even passed the whole process.
Different providers use different approaches to guarantee that the person on the other end of the line is alive. Flashing random-colored lights and watching the reflection on the face, 3D parallax mapping, random prompts to turn heads in different directions – all of those require at least some input from the user.
To make the process truly seamless, we have developed a fully passive approach to liveness detection. A single selfie tells us, through checking for several telltale signs, whether a person is indeed alive. 99 percent of genuine users can get through the whole digital onboarding process on the first try. All other active approaches have a lower success rate.
Although AI, especially generative AI, helps fraudsters find new ways of impersonating real persons, AI also helps us detect these new approaches. Deepfakes or video injection prevention are now must-have tools in our Digital Onboarding Toolkit.
” Is the age difference between the selfie and the ID photo similar to that between issuing the ID and now? Do the MRZ data correspond fully with data on the card? All of these could signal tampering.”
- Document OCR
Optical character recognition (OCR) is a very mature technology that has become a perfect fit for digital onboarding purposes. Its capability to correctly read ID documents is not optional: allowing clients to type in their info invites typos and fraudulent attempts. It is why OCR should be able to read IDs even when identity cards are scratched or not captured in ideal lighting conditions.
Apart from getting the correct information from identity documents, OCR also allows us to cross-check all the fields with the so-called MRZ zone. It contains all the information from the ID in a machine-readable (hence MRZ) format with a checksum. If anything on the ID has been forged, the checksum would not check out, pointing at the forgery.
Apart from reading the document itself, the algorithms also provide cross-checks between different data: Is the age difference between the selfie and the ID photo similar to that between issuing the ID and now? Do the MRZ data correspond fully with data on the card? All of these could signal tampering.
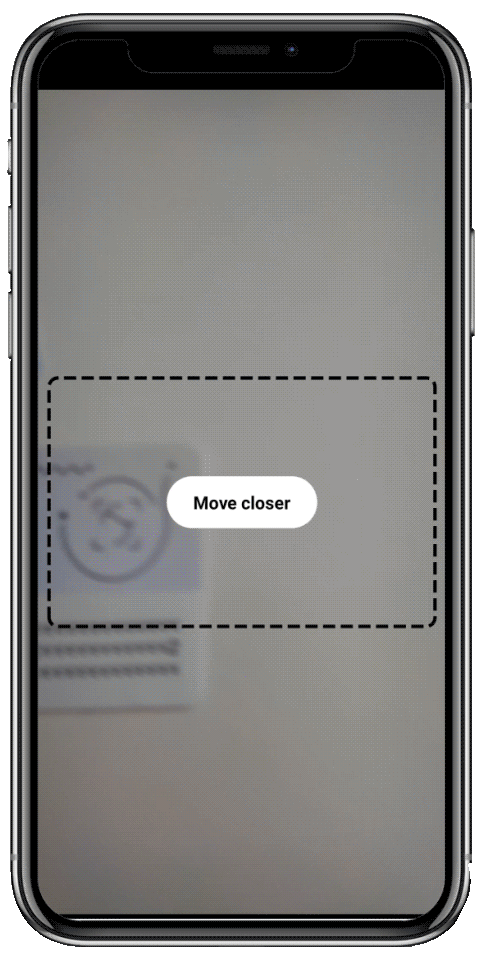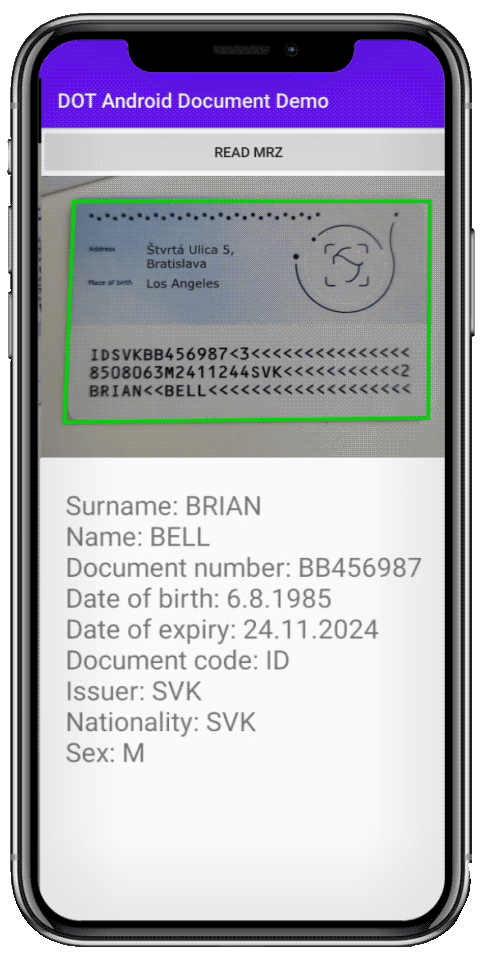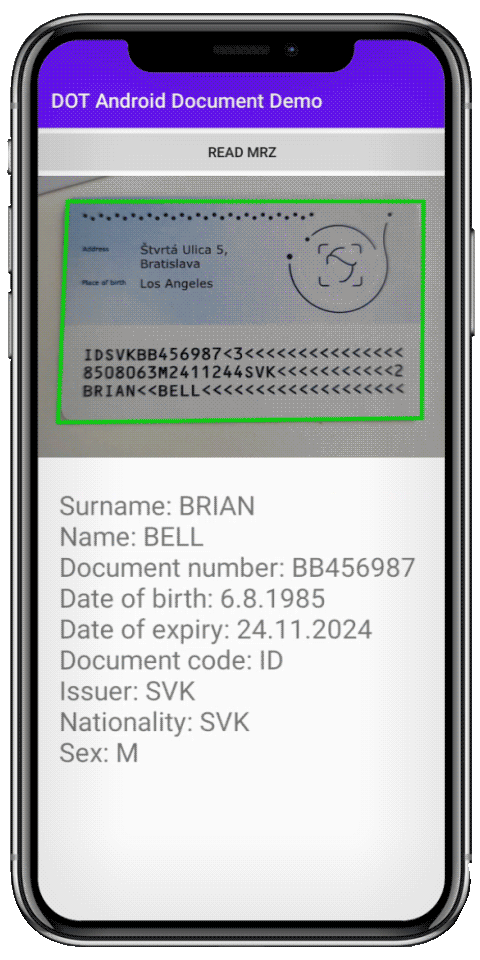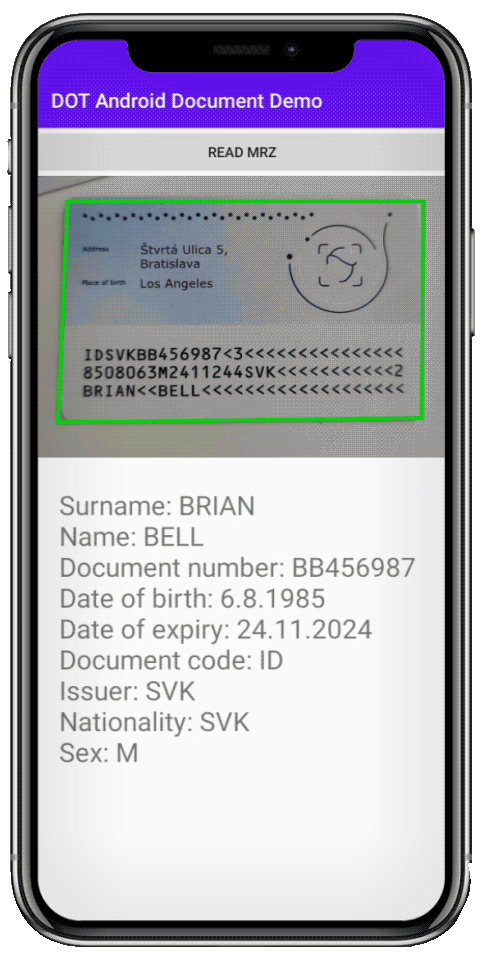
Another standardized technology that can make ID cross-checking even easier is NFC. It is routinely deployed in biometric passports and makes the ID check a breeze because it contains all the required information on a tamper-proof chip. Another upside is that practically all smartphones contain NFC reading capability by default.
More and more IDs, not just passports, support NFCs, making them viable tools for remote identity verification in the upcoming future. NFC chips contain high-resolution user photos, with at least two fingerprints, and have a space for other biometric data – including iris or DNA. These can be compared to the ID holder’s biometrics to ascertain their identity.
A simple piece of practical advice when doing digital onboarding: don’t allow the user to upload images for onboarding. This only invites fraudsters.
A simple piece of practical advice when doing digital onboarding: don’t allow the user to upload images for onboarding. This only invites fraudsters. If you are worried about photo quality, take it through auto-capture. That way, you’re in control of the image quality.
Like OCR, finding the best shot of a face or ID is not an optional feature. The service provider gets the best picture for comparison or reading purposes. Moreover, it makes digital onboarding available even to people unfamiliar with smartphones due to poor eyesight or other disadvantages.
Auto-capture module continuously observes head movement and lighting conditions and can instruct the user how to move their face to automatically take the perfect picture. The same goes for ID, which can get blurry if not taken with enough care.
Technically, a small algorithm constantly evaluates so-called ICAO parameters: head tilt, pitch, jaw, and angle it’s facing. ICAO has standards set for optimal passport pictures and the algorithm takes the shot as soon as the face is close to this ideal. Avoiding user interaction also makes the process faster and prevents some fraud attempts.
All the parts of the whole onboarding process pass a so-called confidence score to the operator to provide it with transparency about the algorithm decision-making. For integrators this also means that the process can be customized based on confidence scores, informing how to process every step. If the face match is not confident enough, it can be retaken or passed on to a human operator. The same goes for the liveness check.
The ID OCR provides a confidence score for every single field on the ID. Only those fields that haven’t been reasonably well read can be corrected by the user, preventing typos and cutting down the onboarding time.
Confidence scores can be used to evaluate the quality of the process, find the bottlenecks, or spot new fraud attempts. They can also be loosened or tightened based on customer satisfaction surveys or other inputs. By tuning confidence scores, the digital onboarding process can be customized to each specific use case.
Sometimes legislation allows for checking against citizen registries, providing extra security to the remote identity verification process. Some countries, like Mexico, even require biometrics-based authentication with a state-run registry. By checking the ID numbers of faces, the registries can quickly warn that the ID has been forged or recently stolen.
Looking for all or some of these technologies ready for easy integration? Contact us.
(You can find other parts of the Elements of Digital Onboarding Series here)