What is biometric identification and personal identification?
Biometrics, as a means of personal identification, relies on who you are as opposed to traditional approaches to personal identification that rely on what you have. Token-based identification (passports, driver’s licenses, ID cards, keys, badges) or knowledge-based identification (password or PIN) both represent obvious disadvantages. They can all be stolen or shared and forgotten, or guessed by an impostor. Modern biometrics, on the other hand, allows not only reliable and instant identification, but also differentiation between an impostor and authorized person. Moreover, biometrics is able to deliver on negative recognition such as preventing a terrorist from boarding an airplane.
Biometrics: authentication or verification
In short, verification is a biometric system function that performs a one-to-one comparison to determine whether the identity claim (e.g., “I am enrolled as subject X”) is true. Verification is typically used for positive recognition (see Positive identification), where the aim is to prevent multiple people from using the same identity or more specifically to prevent unauthorized persons from using someone else’s identity. Biometric verification is also called one-to-one comparison (1:1).
Biometric identification
In short, biometric identification is a one-to-many process of comparing submitted biometric data against some or all records of a database to identify the respective person. Identification provides a candidate list of possible matches.
Biometric authentication or verification is 1:1 comparison and the result is a comparison score used in combination with a threshold to form an access policy. Biometric identification is 1: N comparison, and the result is a list of possible matching candidates.
What are the advantages of biometrics?
You cannot forget to bring yourself, and only biometric technology can provide negative identification (confirm that you are not in the database).
Biometrics can be replicated and biometrics systems are not foolproof (although if the system is properly set up, the security can be very high).
What is biometric information?
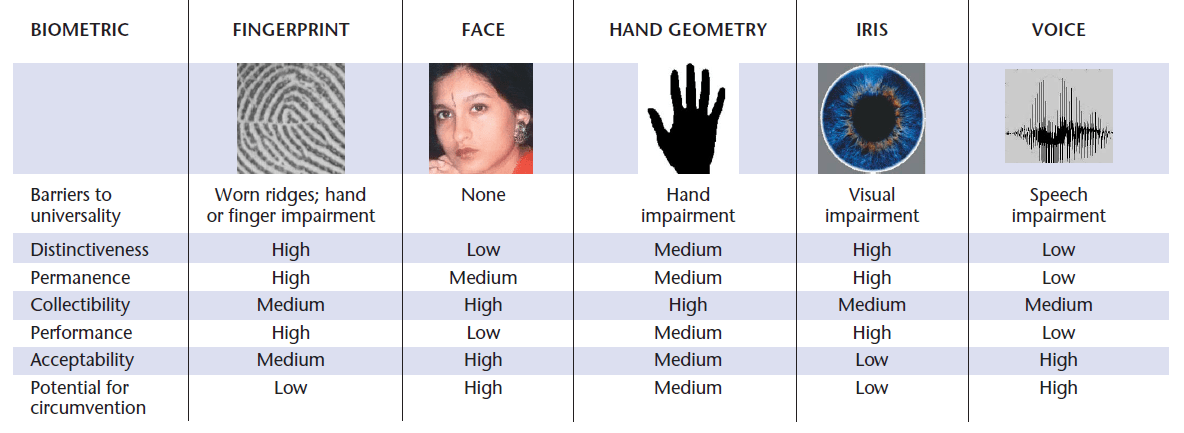
Any human physiological or behavioral trait can serve as a biometric characteristic as long as it satisfies the following requirements:
Universality – Each person should have their own characteristic.
Face and Iris are generally available for all people. Fingerprints may be hard to collect due to damage, especially for manual workers. Therefore, the universality of fingerprints can be lower.
Distinctiveness – Any two persons should be different in terms of their characteristics. Fingerprints and Irises are highly distinctive for different people. Faces, on the other hand, are often similar.
To prevent online fraud, other different behavioral patterns that are specific to the user, such as the rhythm and cadence with which they usually type on their computer keyboard are being explored. Handwriting, particular walking style, body movements, or event recognition can be analyzed as supporting means of personal identification.
Permanence – The characteristic should be sufficiently invariant over a period.
The change we consider is in terms of comparison criteria. Therefore, even though the person’s face changes a lot during a lifetime, some characteristics do not change that much and remain the same.
Fingerprints and Irises remain stable after a few years, during which they develop their permanent shape.
Collectability – The characteristic should be quantitatively measurable.
While the face is easily collected using a normal consumer grade camera, for irises and fingerprints, we usually need special sensors and personal cooperation.
* Different approaches to collecting fingerprints with smartphone cameras are being explored and tested.
For the above mentioned requirements, the most widely used behavioral characteristics in modern biometrics are voice and signature. The most popular physiological traits on the other hand are fingerprint, face and iris.
Other biometric characteristics such as vein pattern or DNA can be extremely reliable in terms of distinctiveness or permanence, they represent significant limits in terms of collectability making their use less popular or limited to certain specific cases.
What are the most used biometric identifiers?
Fingerprint recognition in biometrics
A fingerprint is an impression made by the papillary ridges on the ends of the fingers and thumbs. Fingerprints afford an infallible means of personal identification because the ridge arrangement on every finger of every human being is unique and does not alter with growth or age.
Fingerprints captured in the system are located by minutiae points – points at which scars begin or terminate. These are further mapped with lines between them, creating a minutiae template.
Face recognition in biometrics
A face recognition system is a computer application for automatically identifying or verifying a person from a two- or three-dimensional digital image or a frame from a video source.
Although less accurate than fingerprint recognition, facial recognition technology is often favored because of its contactless nature. Face recognition is mostly used in personal security, law enforcement, or digital onboarding in finance and telecoms.
Face recognition can also be used to perform liveness detection.
Iris recognition in biometrics
Iris recognition is an automated method of biometric identification, taking unique patterns within a ring-shaped region surrounding the pupil of each eye. Iris recognition is an extremely reliable and accurate identification method with very low false match rates. However, iris recognition has some disadvantages such as requiring specialized hardware equipment.
Iris recognition is widely deployed for identification and verification at government and law enforcement levels, but iris recognition is also beginning to make a mark in mobile authentication and access control spaces.
How do you capture biometric information?
Electronic biometric records are collected using a biometric device or biometric scanner. The collected biometric information is then recorded into ABIS, which is used to store and process biometric data for analysis, identification, or verification operations.
Enrollment is the process of capturing biometric samples, processing them to create a biometric template and storing the templates (usually with additional data) onto storage, such as a database or a chip.
Enrollment is necessary to create a reference database that will be used later in our use case, be it passport issuance, blacklisting using CCTV solution or border crossing. Without the reference database, we would not have anything to compare with.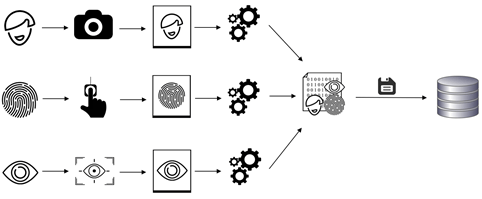
What is biometric data?
Biometrics and biometric data are related to the measurement and statistical analysis of people’s unique behavioral and biological (anatomical and physiological) characteristics or traits.
According to EU data privacy regulation, biometric data is “personal data resulting from specific technical processing relating to the physical, physiological, or behavioral characteristics of a natural person, which allows or confirms the unique identification of that natural person, such as facial images or fingerprint data.”
What is a biometric system?
Biometric systems use personal characteristics (directly linked to who you are) to authenticate or identify an individual.
Multimodal biometric systems can combine multiple biometric traits, resulting in a biometric identification that is robust and more distinctive.