How eKYC can make sharing economy apps safer


Mandatory in highly regulated fields like banking and communications, the Know Your Customer (KYC) process is a crucial part of onboarding for many companies. But would it also enhance trust on sharing economy platforms? We explore how electronic KYC that uses biometrics would make it easy, effortless and safe for both platforms and users.
In this brand-new world of opportunities, the rise of the sharing economy has brought about some concerns: episodes of fraud, identity theft, money laundering and violence. This is partly because this economic sector – which has expanded at supersonic speeds in recent decades – also typically lacks stringent rules and regulations.
Sharing economy companies are responsible for ensuring their platforms are a safe and stress-free space for people who use them. So how can they ensure a credible and trustworthy space? Biometrics offers an answer, and as the sharing economy continues to evolve, there’s much to be learned from other industries. Let’s explore some of these lessons.
Building reputation
In 2020, a small team of scientists from the Technical University of Darmstadt conducted an online survey with 232 participants. They created simulated sharing economy profiles, some with verified user identities and some without. Their findings were clear: verifying user identity on sharing economy platforms increased trust. But trust wasn’t just about identity verification; the reputation of the platform itself played a significant role in building trust among users.
KYC in regulated fields
Let’s look away from the sharing economy for a moment, and we find some industries governed by stringent regulations. Here, the onboarding process for new clients must follow standardised procedures, including the crucial step of identity verification. They call such protocols: “Know Your Customer” (KYC). It’s the first contact between a company and a client, and a key moment in establishing trust and security.
While KYC protocols initially took root in sectors such as banking and finance, their importance has gradually spread to non-financial sectors such as real estate, healthcare and gambling.
During the KYC process, the company asks the customer for documents and verifies their identity. This used to – and still is in many fields – be done manually. For example, manual KYC for a bank customer means a person needs to go to a bank branch, present their documents and have a bank employee check them.
Thanks to biometrics, and especially facial recognition, these manual checks can now be easily omitted and substituted with remote facial recognition algorithms. This is known as “Electronic Know Your Customer”, or eKYC.
At a glance: KYC vs. eKYC

Traditional KYC varies from one type to another. But it usually involves at least one of the following aspects:
- Physical presence of the customer
- Manual submission of documents
- Manual verification of the documents
It is, therefore, costly, time-consuming, geographically dependent and subject to human error and potential fraud.

Electronic Know Your Customer follows standardised paths and certifications, typically involving:
- Remote verification: the customer is not present in person – their biometric parameters are verified by digital technology that analyses facial features, fingerprints or iris/retina patterns
- Documents are all submitted online
- Identity verification is enabled by biometrics, artificial intelligence technology and machine learning
eKYC is faster than traditional KYC, less prone to error and fraud, and doesn’t depend on physical location.
The dark web
A little bit of everything can be found on the dark web: weapons, drugs, passwords – including compromised accounts on sharing economy platforms. Interestingly, hacked accounts often fetch a higher price compared to credit card information. The reason behind this is the sometimes sluggish response of platforms, which provides criminals with a larger window of opportunity to cash in.
eKYC for companies and governments
Making the KYC process quick and easy is essential for both customers and companies during onboarding. Slow, complicated processes tend to discourage potential customers. For example, in Indonesia, about 40% of online registrations aren’t finished as users give up because the onboarding processes are too long and complicated. This data inspired the company ASLI RI – a global identity leader based in Indonesia – to look for a way to build eKYC systems for their business partners.
They wanted to build a fully customisable eKYC system that could be used for both civil and commercial purposes to onboard new customers or citizens. They found a solution in remote identity verification using biometrics, especially face recognition, and liveness detection – all based on the Digital Onboarding Toolkit (DOT) from Innovatrics. With the security level offered by DOT, ASLI RI has been entrusted with integrations to several Indonesian government agency databases: National ID, National Police, and the National Narcotics Agency, to provide secure identity proofing nationwide.
Today, ASLI RI is the number one identity provider in Indonesia, with 10 million users processed annually. They offer their eKYC system in sectors like border control, criminal investigation, national identification systems, voter registration and commercial KYC.
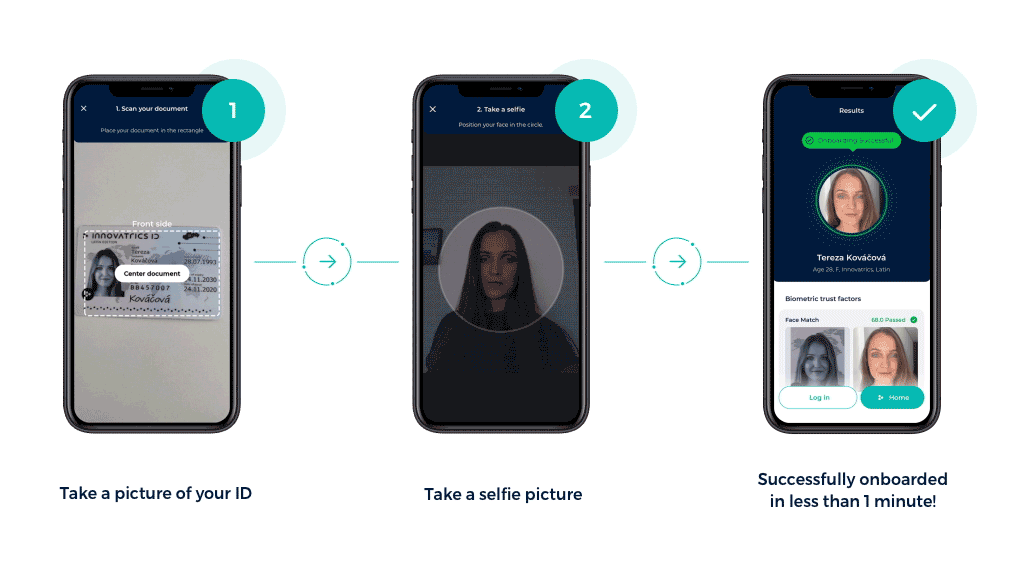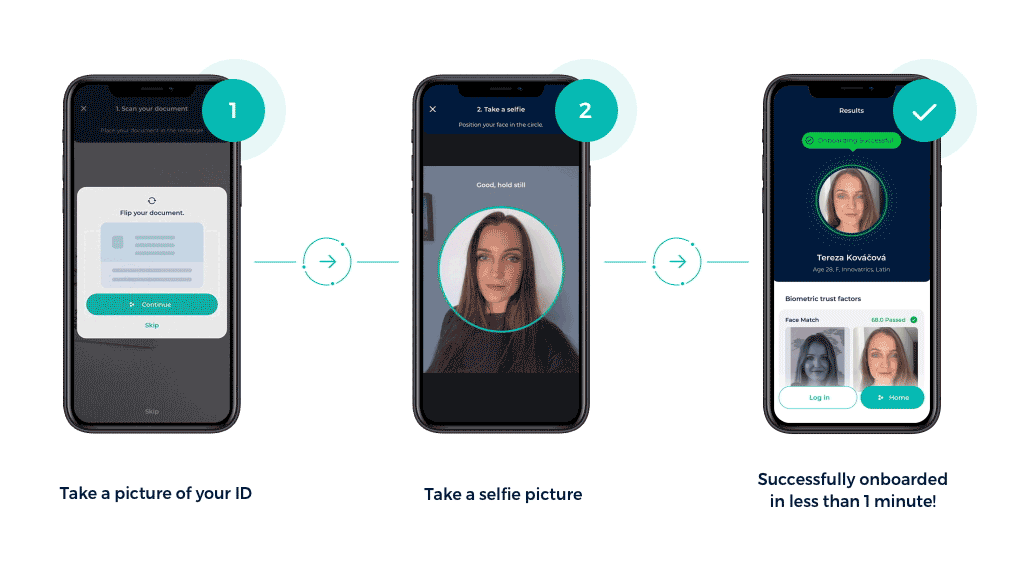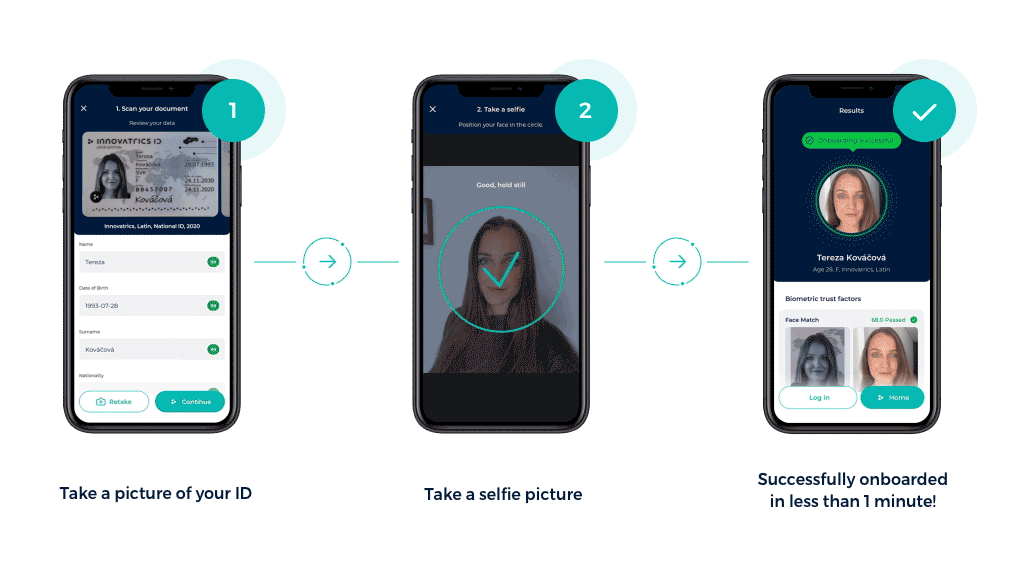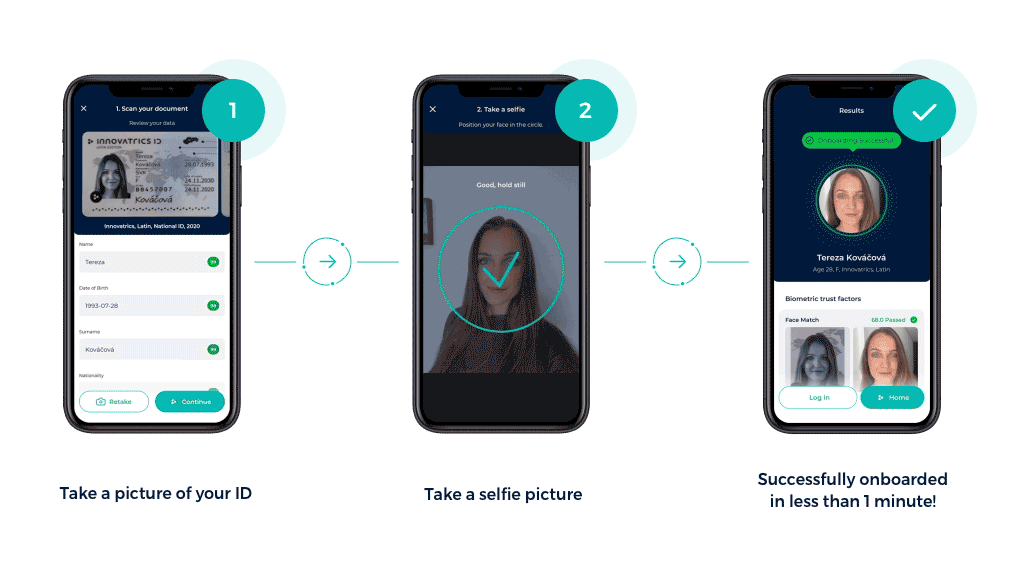
Electronic Know Your Customer, step-by-step
- Basic information
The first contact between the user and the company. It usually starts with basic information such as their name, address and contact details. - Upload document and take a selfie
Customers submit a digital copy of their documents – this could be a government-issued ID, passport or driving license – and are then asked to take a selfie or record a short video.
- Verifying data
Using AI and machine learning algorithms, the system verifies the consistency of all the information and documents provided by the user. The eKYC systems check for false information, inconsistencies and tampering. Proofing might be backed by integrations with government databases.
- Securing data
Verified information is stored securely by the company according to international standards and privacy regulations. Suspicious transactions in user activity are monitored to identify potential fraud or account breaches.
Igor Jánoš

Image Data Synthesis Lead at Innovatrics
Identity verification: Finding the “sweet spot” between security and user-friendliness
Together with Igor Jánoš, we explore how to find a balance when choosing how many false matches you are willing to accept when using biometrics for remote customer identity verification and onboarding, and just how much you are ready to test your customers’ patience.
We know that no algorithm can be 100% accurate. So how do we decide just how much room for error is tolerable?
Generally speaking, the level of error we are prepared to tolerate depends on the potential danger a mistake might cause. So with low-level danger, we can tolerate higher risk, and vice versa. But we should also always take into consideration the size and type of data we are comparing. For example, if 10 of my friends are coming for dinner and we’re checking that the photos they have submitted match the “dataset” of 10, there is rather a big chance there won’t be any lookalikes in the group. But when comparing photos against a dataset that contains millions of people’s information, there could be dozens. So we have to decide just how big of a risk of people looking alike we are willing to accept, and what the chances are that we will let somebody in who we shouldn’t.
What if the company feels there is no room for error?
In this case, it is possible to create a sort of “grey area”. For example, in an instance of two people being too similar to prevent a 100% negative match, but not enough to confirm a 100% positive match, there is an option to create another layer of verification: manual. But it’s up to the company to decide where they set this threshold, because with manual verification you also have to consider both time and economic factors.
And what exactly is the threshold you mention?
To put it simply, the probability of verification is marked in numbers from 0 to 1, with 1 being completely certain of a true positive or true negative. Then we have false positives and false negatives. A false negative means we decline a match that should in fact be accepted. A false positive means we incorrectly approve a match that in reality is not one. The first case means we irritate the customer, as the process is slower than desired, they are asked to take another photo, and so on. But the second case can create a much bigger risk, as we are essentially granting “access” to someone who shouldn’t have it. These 0 to 1 values enable us to set thresholds that balance these two “false results”.
To refer to false positives or false negatives we use rates like 1:10,000 or 1:100,000 and so on. These are very small numbers that relate to very few mistakes, but, they are there. So when the client sets up their software for remote identity verification they need to decide how many of these potential mistakes they are willing to tolerate, and what to do with them. Are they OK with the risk of false positives? Or do they want to verify any unclear results manually? It is up to them.
Ok, so false positives can be a riskier problem, and false negatives mostly just annoy customers. But companies, especially those in the sharing economy industry, don’t want to annoy their customers.
The easiest way to avoid this and make identity verification user-friendly is to help users take the best selfie possible on the first try. When a person takes a photo for identity verification and the photo is bad quality, the chance of a false positive or false negative is much higher. That’s why it’s important to guide users to take good photos. People may not realize that, for example, a small change in angle can change the way the algorithm reads their facial points, which can lead to errors in the comparison results. This is why we use selfie navigation in our Digital Onboarding Tool (DOT), so that the angle, distance, and light of the submitted photographs are optimal.
So to answer the question about how to find a “sweet spot” between security and user-friendliness, the best thing a company can do is to help its users take the best selfie possible?
Yes, as this eliminates a lot of unnecessary false negatives. There is then also the decision about adding another layer of security for potential false matches – the manual control.
Are there other factors to consider?
Well, yes, every decision has some consequences. For example, DOT also provides a liveness check, which is very useful for combatting attempted fraud attacks such as people using photos of others, or masks, to try to fool the algorithm – but this makes the whole process a little bit slower. Also, the company needs to decide on the size of the algorithm model they want to use. The bigger the model, the more precise the results, but the response time is also higher – plus you need to think about the infrastructure. Smaller models can run on smaller devices such as smartphones and are quicker to use, but have, obviously, a smaller capacity.
The onboarding experience
of a Malaysian delivery app
eKYC makes it easy to verify users’ identity from anywhere, which is a quality sharing economy platforms that are decentralised could benefit from. One such platform that is considering eKYC is Halo Delivery, a major same-day delivery app in Malaysia. We talked about the possibilities and challenges of eKYC with the company’s CEO and founder, Jalluddin Abu Hassan. What would a remote identity verification process bring to the delivery platform?
Launched in 2019, Halo Delivery now has almost 1.4 million customers and a community of over 30,000 merchants and 3,000 active riders across the country. The app focuses on suburban areas and underserved markets, allowing users to order food, pharmacy products and other goods.
Like most sharing economy businesses, Halo Delivery doesn’t use eKYC protocols, but it does have an onboarding system for new clients and drivers. It’s mainly digital, but there’s some manual operation too. There are two users of the app – customers and drivers.
To open an account and start using the app, customers have to fill in a quick online form. They give their name, telephone number and email address. When they place their first order, they also have to add their physical address. If they pay digitally and the payment goes smoothly, the verification is 100% complete. If customers want to pay cash when they receive the order, another manual verification step is added: a phone call by the drivers. If the customer doesn’t reply to the call or call back in a reasonable amount of time, the user is labelled as a “fake user” and the order is cancelled.
From the perspective of CEO Jalluddin Abu Hassan, who is also a member of the Malaysian Institute of Accountants and Institute of Marketing Malaysia, an improved digital verification of customers could help to reduce the number of customers wrongly labelled as fake.
As for the drivers, to use the app they have to upload a copy of their ID card and their motorcycle license, which is manually checked by staff to assign them the right insurance coverage. Expired licenses or fake accounts are often discovered only in the event of an insurance claim or accident, whereas an eKYC checks the driver’s credentials immediately.
Since eKYC is not geographically dependent, it also plays an important role in expanding into other markets. For Halo Delivery, that is Indonesia. But there are reservations too. Jalluddin Abu Hassan makes it clear that eKYC shouldn’t make things more complicated for customers and drivers. “Delivery is about time sensitivity, so it’s important that no extra steps are added to the current experience,” he says, adding that a smooth user experience is important since drivers in Malaysia are sparse and operate on more than one platform.
Although it would give them a competitive edge and build trust, currently there’s no regulatory pressure forcing sharing economy platforms to use eKYC and remote identity verification.
Inspired by fields like banking, finances and communication, we see that KYC – and especially eKYC utilising biometrics – can streamline the onboarding process, eliminate geographical barriers, reduce the risk of error and fraud, and enhance the overall user experience. And those are factors that all sharing economy companies and their users can benefit from.
AUTHOR: Giovanni Blandino










