Six must-haves for a trusted election via smartphones

We go online to send money, manage our health, take classes and buy groceries – so why are we still unable to vote via our smartphones? Governments often cite risks of possible hacks and security breaches, which are said to have greater potential to affect online systems than traditional processes. But is that really the case?
In reality, online voting could increase voter turnout as well as avoid fraud and mistakes. Plus, sooner or later it’s also bound to be a matter of public expectation. Let’s find out what we can learn from the pioneer in online voting, Estonia.
Estonia has allowed its citizens to vote online for national, local and European elections since 2005. Citizens can vote from anywhere – their homes, offices, or even while they are on vacation – using any of their personal devices: smartphones, laptops, tablets. When you think about the possibilities, online voting has the potential to be a great thing. It’s more convenient, the results should be more accurate, human mistakes could be avoided and counting would be easily repeatable. Nevertheless, many democratic countries see online voting as a taboo – and its potential still remains untapped.
Hacks and sabotages are more than legitimate concerns when it comes to safeguarding the heart of the democratic system. Still, Estonia shows us that it is possible to vote online securely, and in a way deserving of citizens’ trust.
So, how can we make voting via smartphones a reality?
Authentication in traditional elections
During in-person voting, one or more election officials manually verify the ID of the voter to prevent scams and check if the voter is inscribed in the electoral register. As secure as this method can be, it requires a certain amount of time.
Mail-in voters usually verify their identity by communicating data such as their ID number or date of birth on a form that is attached to the ballot. To impersonate a voter, a thief would therefore simply need to obtain that information plus the ballot.
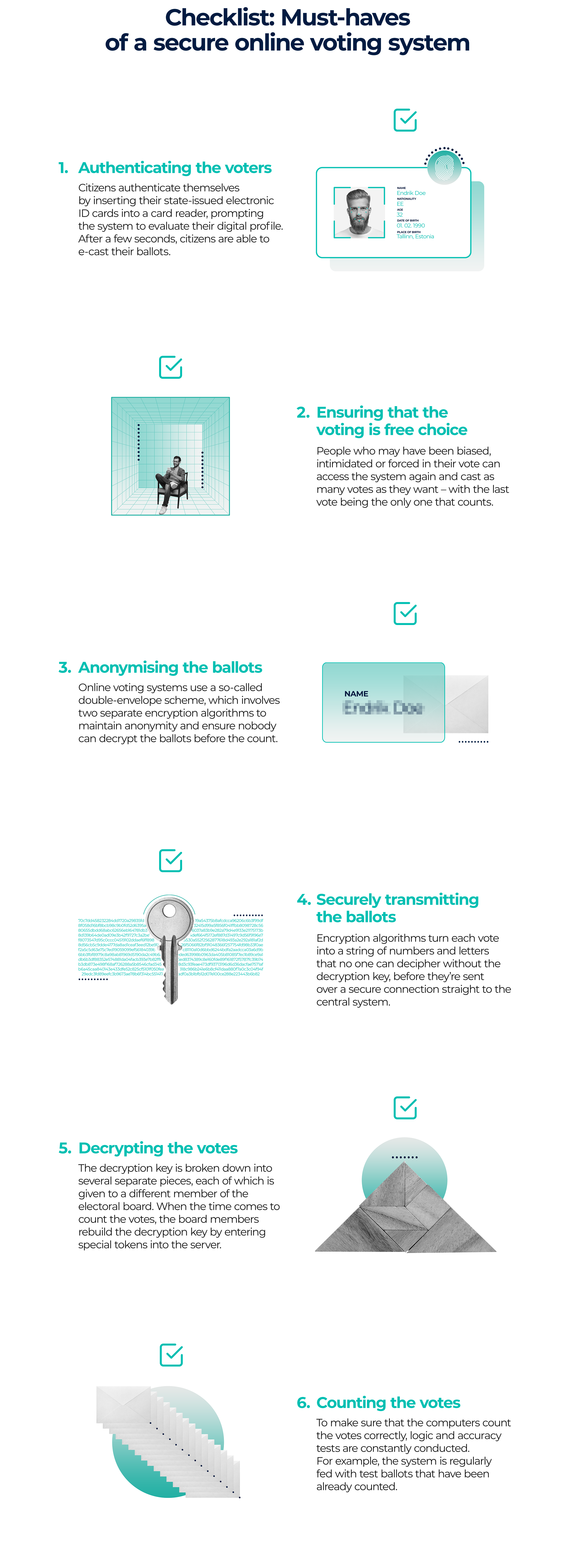
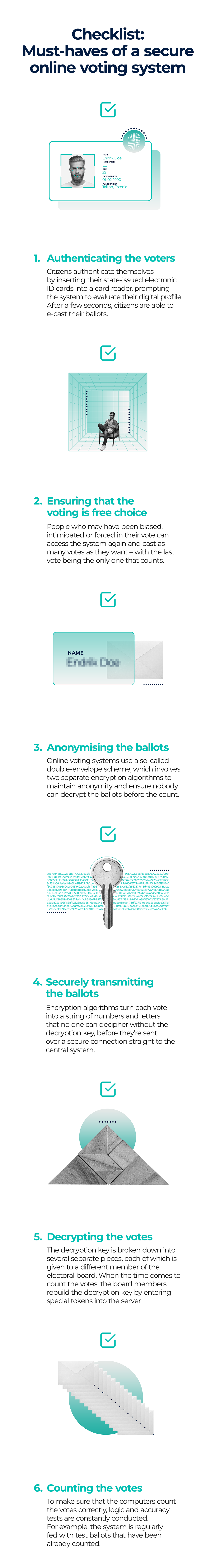
1. Authenticating the voters
Any electoral system must ensure that only legitimate voters are casting a ballot: no deceased people, for example, or identity thieves. Knowing who is voting is the responsibility of a decent voting system – so how does it work in online voting?

In Estonia, 99% of citizens have a state-issued digital identity, and this makes the job half done. Basically, every Estonian has a digital profile – containing personal information like place and date of birth and biometric data – that is stored in their own electronic ID card or in a special mobile SIM card. This allows citizens to access a diverse range of digital services, from tax declaration to e-health. And this digital identity can also be used to authenticate voters.
To cast a vote from their smartphone, for example, Estonians insert their ID cards into a card reader and then enter their PIN code. The system reads the digital profile and checks whether the citizen is eligible for voting or not, and after just a few seconds, the eligible voter is then ready to e-cast their ballot. In the future, biometrics may be used to ease this authentication process.
2. Ensuring that the voting is free
No coercion, no threats and no intimidation of any kind must be allowed to impact voters.
One of the biggest objections to online voting is that it happens in places that can’t be monitored – it does not happen in a polling station or in an embassy, it can take place anywhere. So how can you be sure that citizens are voting according to their own true will?

Sometimes the best solution is the simplest one. Without the use of any tech fix, online voting systems usually resolve this coercion issue by allowing voters to cast as many votes they want – with the last vote being the only one that counts. It’s simple, and it works.
People who may have been biased, intimidated or forced in their vote can access the system again at a later stage and cast their actual vote. In Estonia, online voters may also visit a polling station after having voted online: in-person ballots have supremacy over the e-vote.
Voter anonymity in traditional elections
Maintaining voter anonymity also represents a challenge for more traditional ways of voting. Clandestine cameras at poll sites can be used to expose voter identity, while latent fingerprints left on ballots might also be used to link voters to their ballots.
3. Anonymising the ballots
The vote is secret – this is one of the essentials of any democratic electoral system. Although the identity of the voter must initially be verified in order to let the voter cast the ballot, it must in no way be linked with their preference.
To anonymise the ballots, online voting systems use a so-called double-envelope scheme. This is a classical scheme that also works in the analogue world. Imagine two envelopes, one inside the other. The inner envelope contains the vote, the outer envelope contains the voter’s name. The so-assembled bundle arrives at the teller: the outer envelope is opened, the name is checked to make sure the voter is eligible, and then disposed of. Only the inner envelope remains, still sealed and containing the vote. This is mixed in the ballot box with all other votes.
Online voting basically replicates this “old-school” scheme: yet instead of envelopes we have separate encryption algorithms that secure each part of the vote, maintaining the anonymity as well as ensuring nobody can open (or decrypt) the ballots before the counting. When ready to count, the first round of decryption is done to the “outer envelope”, i.e. the voter’s name. Once approved, the “inner envelope”, still encrypted, is then added to the digital ballot box. The digital anonymisation goes even further than the manual version, however, as the secret votes are mixed several times through a chain of servers before being decrypted, making it even harder for would-be hackers to trace back to a voter’s identity.
4. Securely transmitting the ballots
During an online election, as votes leave the voters’ smartphones they are sent to a virtual central ballot box where they will then be tallied. How to ensure that votes are not tampered with along the way? And how to prevent that information from being revealed to prying eyes?
This is a critical point, and it is much emphasised by critics arguing that hackers would exploit any security flaw in this transition. Yet, with the right measures, transmitting votes can be completely secure.
Two things are needed to safely transmit an electronic vote. First, the information must be encrypted – meaning it’s only possible to be read by the intended, legitimate people – and second, it must be sent over a secure connection linking the smartphone with the central system.

Put simply, encryption algorithms turn the vote into a string of numbers and letters, something that looks like this: 7hjkaouy84uhalk001klosokcbnz. Obviously, no one can understand the meaning of the string, unless they have the only thing that can turn it back: the decryption key.
Encrypted votes are then sent over secure connections. Popular protocols are employed here, such as the Transport Layer Security (TLS) used by PayPal, among others. The security of these channels is also guaranteed by cryptography.
5. Decrypting the votes
Votes have now reached the virtual ballot box. They are stored in a highly secure server, which is called an air-gapped server – a set of computers physically isolated from any other network to prevent them from being reached by any malicious actor.
Votes will then be decrypted by the electoral committee and tallied. As mentioned, a private decryption key is needed to read the votes. This key is perhaps the most important thing to be kept secret and secure: anyone who gets their hands on it could sabotage the elections of a democratic country.
The decryption key is thus broken down into several pieces, with each one given to a different member of the electoral board. In Estonia, for example, each one of the seven electoral board members has a token. The token is stored in a smart card or USB device, protected by a PIN code. When it comes time to count the votes, the electoral board members must enter their tokens into the air-gapped server to rebuild the decryption key. A minimum quorum is needed to generate the key.
Counting the traditional way
Most democracies collect votes in traditional ballot boxes, which then require armies of poll workers – or, more recently, automated scanning machines – to tally the results. The counting of paper ballots has an estimated error rate that ranges from 0.5% to 2%.
6. Counting the votes
Finally: the vote counting. The tallying is usually operated by the air-gapped computers.
In Estonia, to make sure that the computers count the votes correctly, logic and accuracy tests are constantly conducted. For example, the system is regularly fed with test ballots that have been already counted.
In 17 years of online elections in Estonia, not a single vote has been incorrectly counted.
AUTHOR
Giovanni Blandino
PHOTOS
Shutterstock
SOURCES
Online Voting Isn’t as Flawed as You Think—Just Ask Estonia
Elections and Technology
e-Identity
Ensuring the Integrity of Elections








